Cyber Security : What is Cyber Security? Friends, if you want to know what is cyber security, its definition, how it works and what are its types. If you know then you may not know everything, after reading this article properly you will know the complete information. security or cyber safety is a type of security that is a protection for systems connected to the Internet. Through this, the hardware and software data is made more secure so that the data is not stolen in any way and all the documents and files are safe.
Cyber security is a combination of two words Cyber + Security, which means anything related to internet, information, technology, computer, network, application or data, we call it cyber. It is only related to the security of cyber in which includes system security, network security, application and information security. Further, every point related to cyber security will be discussed, you will have to stay with the article to get complete information.
What is Cyber Security?
Cyber security, also called computer security or information technology security, is a method of protecting data, computers, networks and software from cyber attacks. Cyber security is the practice of keeping any type of information and data available in computers and networks secure and confidential. It is the protection of computer systems and networks from theft or damage of software or electronic data, as well as from disruption or misidentification of the services they provide.
Cyber security refers to the security on the Internet. When you use the Internet or are connected to the Internet, many types of threats remain on you because hackers can access your system by breaking cyber security in many different ways. And they can misuse your personal data, cyber security is used to prevent this danger.
The job of cyber security is to provide security to the devices, software and data and networks connected to the Internet network. In cyber security, your network, devices, software and data are protected by secure layers, so that your data is protected from malicious activities on the Internet.
Cyber security is a protection for systems connected to the Internet that works to protect devices, hardware, software and data from cyber crime, in simple words, cyber security is to protect systems, networks and programs from digital attacks.
You can also read this popular Articles :
Why is Cyber Security Important?
Some reasons have been mentioned below, which show that cyber security is very important:
1. Cyber Security is necessary to keep safe our personal data such as Image, PDF, Text Document or any other type of data which resides in our computer.
2. Cyber security is very important to protect any of our data in which only our copyright is there. For example, if you own a company, only you own the copyright to its data, it is essential that no one steals it or someone else can use it.
3. Cyber security is also very important to provide safety to our banking and financial data because if our banking data is not secure then any hacker can easily withdraw money from the bank account, nowadays baking through internet has become an essential part of life. Therefore it is important to keep banking and financial data secure.
4. For national security Cyber security is also very important. National security means that nowadays cyber attacks are taking place even in the defence system of most of the countries.
5. There are also some secret data or information which are very sensitive and important, because nowadays most of the work in government offices is also done through the Internet. If the secret or sensitive data of any government office gets leaked then it can cause a lot of harmful. Cyber security is also very important to keep such sensitive and more important data safe.
Types of Cyber Crime
Cyber crime is done in different ways, some of which are given below-
1. Hacking: In this type of cyber crime, hackers enter a restricted area and gain access to another person's personal data and sensitive information without that person's permission, the restricted area is someone's personal computer (PC) / Laptop, mobile Or someone online. Can have a bank account (net banking).
2. Cyber Theft: In this type of cyber crime hackers violate copyright law and it is a part of cyber crime which means theft done through computer or internet. This includes information theft, password theft, identity theft, internet time theft, etc.
3. Cyber Stalking: This cyber crime is being seen more in social media sites. In this, the stalker harass the person by repeatedly sending dirty messages or emails. In this, often stalkers make victims of small children and such people who do not have much knowledge of the Internet. After this, the pursuers start blackmailing that person, due to which the life of that person becomes very painful.
4. Identity Theft: This type of cyber crime is being seen a lot these days. In this, hackers target people who use online cash transactions and banking services like Google Pay, Phone Pay, Paytm. Hackers get into a lucrative conversation with a person to get that person's bank account, debit card details, internet banking details then hackers take out all the money of a person.
5. Malicious Software: Many such dangerous software is created by hackers who can not only steal the data of computer or mobile by connecting to any internet but also delete it, also hackers can hack your entire system with the help of these software can crash your entire system.
These software are of many types such as malware, spyware, virus, ransomware and worms. Hackers send this type of software, mostly through links, pop-up messages or emails, to other computers and attractively ask them to touch the links. If that person touches the link, the hacker takes full control of the computer.
6. Phishing: In this type of cyber threat, the hacker sends a message or email to a person posing as a trusted institution or bank, which looks absolutely legitimate. The hacker's motive behind this is to cause financial harm to that person by taking sensitive information like bank account number, debit card etc.
7. Child Pornography and Abuse: In this type of cyber crime, hackers mostly use chat rooms and talk politely by hiding their identity. Young children or minors do not have much knowledge and gradually hackers obstruct children for child pornography. When children become victims of pornography, they are blackmailed and are unable to even tell their parents due to fear.
8. Man in the Middle (MITM) Attack: In this type of cyber crime, the attacker who is the hacker keeps on spying on the communication of two people and after some time becomes one of those two people and the real friend Sounds like talking. Information, and sensitive data such as bank, debit, credit card details etc. Due to this, the person in front does not even know and all the information comes to the hacker.
9. Denial of Services (DoS): The main purpose of DoS attack is to reduce the traffic of a network or website. In this services hackers weaken the targeted network system by suddenly bringing heavy of traffic to a network or website.
Along with this there are many services like yahoo, hotmail or any Email etc. When suddenly there will be a lot of traffic, if a user goes to log in, the user will not be able to use that service.
10. Spoofing: In this type of cyber attack, the hacker can use the identity of another person to attack a large server or system of a large company. A hacker can destroy someone's life by taking the help of this attack.
11. Salami Slicing Attack: "Salami Slicing Attack" is also also known as Salami Fraud. In such cyber crime, cyber criminals make a big attack by doing many small attacks. Attackers use customer information such as bank/debit card details to deduct small amounts of money.
Due to less money being deducted, customers remain unaware of slicing and do not even complain about it, due to which the hacker is not detected. It is just a strategy to make profit from small increments from time to time.
It is true that thieves have a lot of brains so often new types of cyber crimes keep coming up. Apart from these, many more cyber attacks are taking place, with the passage of time new types of them are also being discovered.
You can also READ :
Types of Cyber Security
In cyber security, different security is given to the user in different layers of the network. All the crimes mentioned above are done online and six best cyber security to prevent them are as follows-
1. Network and Gateway Security – This can be called the first layer of the network. You must have heard the name of Firewall in the computer. It's a wall for a network that only allows secure things in and keeps unsafe threats out.
2. Data Loss Prevention (DLP) - In this process all the data of the user is fully encoded using SSL (Secure Socket Layer). Data is encrypted under this protection, to keep it away from unauthorised access. This process increases the security of the data, with no risk of data theft or leaking, i.e. the data is completely encoded.
3. Application Security - By this the applications being used in the network go through a security process. This is done to overcome the shortcomings of the application. Also, if that application is vulnerable then it is taken out of network.
4. Email Security – If you use Gmail, you may have noticed that some emails go to the Spam folder. Email is provided security by installing spam filters in the network. So that harmful emails can be kept out of the reach of the user because most of the crimes are done through email phishing.
5. Antivirus Security - Every person who accesses the Internet or uses external memory on his PC or Laptop installs Antivirus in his PC or Laptop. This antivirus protects our PC or laptop from different types of viruses. Nowadays we all keep our important data, sensitive information and personal files saved in the computer itself. Therefore, keeping it safe is a very important task.
6. Network Access Control - By this the work is done to keep unauthorised users and devices out of the network. NAC protects the functionality of the network, ensuring that only authorised users and devices have access to it. Network operators determine which devices or applications comply with endpoint security requirements through their own specific programming and whether or not they will be allowed network access.
Connecting to the network is a very secure process, in which policies are made according to the users and their network related rights are limited.
Along with all these security layers, an internet user also needs to follow certain rules at their level, such as using strong passwords and not opening unknown email attachments.
If you want to earn online CLICK HERE :
Benefits of Cyber Security
➤ With the help of this, we can stay safe from Unauthorised Access, which will not cause any kind of data loss.
➤ we can keep our network secure with the help of cyber security, so that we can use the internet with confidence.
➤ Very strong a security cover is provided to your sensitive data and personal data so that hackers cannot exploit you financially or mentally.
➤ Information security improves and business management also increases.
➤ Online cash transactions are very much in vogue these days, so you can do secure transactions with cyber security.
➤ Malware damage is preventable, including viruses, spyware, worms, ransomware, adware and a variety of threats that can threaten data and devices.
➤ The data is secure, reducing the risk of important data being leaked or stolen.
➤ Security is provided to the network, so as to prevent unwanted access from entering the network.
➤ Along with external security, restrictions can also be placed on network users, thereby curbing unwanted activities.
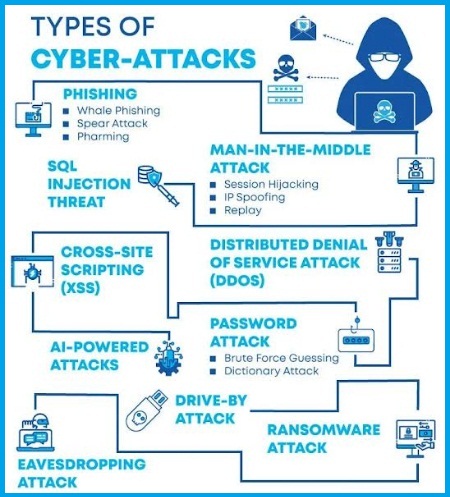
Types of Cyber Attack
From the above picture you can understand very easily what are the types of cyber attacks. Now I will discuss this topic-
Malware:- Malware includes all types of malicious software, such as spyware, ransomware, viruses and worms, most of the main sources of such threats in a computer or network are links and email attachments. In which if a user clicks, the software or script is run, after which the user loses control over the computer and all services connected to the network are blocked and spyware starts transmitting data.
Phishing:- In this, emails are sent to the users in the name of reputed institutions, and personal information is sought, such as important information related to debit cards and credit cards etc. and we all know that nowadays it has become a very common thing..
Man in the Middle (MITM):- In MITM attack the communication between any two people is tampered with by the attacker, i.e. the communication between the two is controlled by the attacker, which is not known to the user. remains, and all necessary information reaches the attacker.
Zero-day:- In this, any software flaw is targeted by the hacker, whose software publisher is not aware, and the software is completely tampered with before the publisher removes the recovery patch. ,
Apart from all these cyber security attacks, there are also many types of threats, which can harm the internet user.
Conclusion
Knowing what is cyber security is not enough. The best way to avoid cyber crime is that you do not click on the link of any tempting message, if you do this, then check the URL of that link as well to see if there is a spelling mistake in it. Plus, create a strong password for any of your accounts that includes uppercase and lowercase characters, and be safe.
Friends, you also learned in the article that how many types of Cyber Attacks, and how a network can be protected from such threats, for which the option of every level of network security is also available. To stay safe on the Internet, along with all the security devices and applications, it also depends on the user's functionality, that is, an End User should also take every small step from the point of view of security while working on the Internet, which can threaten Cyber Security.




0 Comments