Posted By: technopediasite
Protection architectures
There are two fundamentally different protection architectures for APS,
- Linear protection --- linear multiplex section protection (linear MSP) point-to-point links.
-Ring protection -- multiplex section shared protection ring (MSSP ring) according to ITU-TG.841 and ANSI T1.105.1 for ring structures.
Both these protection mechanisms make use of alternate circuits or components. The signaling procedures required for the switch-over are transferred in overhead bytes K1 and K2 of the SOH (SDH) or the TOH (SONET).
The three different protection mechanisms
1+1: - Traffic is transmitted simultaneously on the working line and the protection line.
- Both lines transport 100%traffic.
- In the event of a fault, the receiver is switched over to the protection line.
1 : 1: - Traffic is transmitted on one channel only.
- No traffic, or only low-priority traffic, is transmitted on the protection line, 100% protection.
1 : N: - Traffic is transmitted on the working line. No traffic, or only low-priority traffic, is transmitted on the protection line.
- N lines share one protection line.
- In the event of a fault, the protection line takes care of the traffic on the defective channel.
- Common, economical protection method.
Automatic protection switching (APS) is a fault-tolerant topology that is used for providing backup to telecom networks. For network survivability, in the event of failure in a network element or link, APS involves reserving a protection channel with the same capacity as the channel or facility to be protected. In the event of signal-fail (SF) or signal-degrade (SD) condition, the working line switches automatically to the protection line within a few milliseconds.

Network failures, whether due to human error or faulty technology, can be very expensive for users and telecom service providers alike. As a result, the subject of so-called fall-back mechanism is currently one of the most talked about in the telecom world. A wide range of standardised mechanisms is incorporated into synchronous networks in order to compensate for failures in network path/elements and to provide highly-available telecom networks.
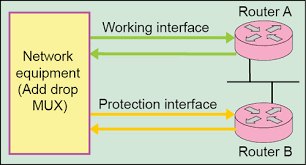
The simplest form of protection switching is referred to as 1+1 APS. Each working line is protected by one protection line. If an alarm occurs, a switch-over is initiated at both ends of the connection by the protection agent integrated in the network element. The switch-over is triggered by a defect (e.g. LOS). The switch-over at the opposite end is tripped by a feedback signal in the reverse direction.The 1+1 architecture is 100% redundant. There is one protection line for each working line. The 1:N
architecture is preferred for long-range networks for reasons relating to cost. Here, several working lines share the same protection line.
The 1+1 and 1:N protection mechanisms are standardized in the ITU-T Recommendations. Protection lines can be used for low-priority traffic, which is however interrupted in the event of a switch-over.


Ring protection
- Unidirectional and
- Bidirectional ring structures
Unidirectional rings: The information is only transmitted in one direction. A connection to a
neighboring network element may consequently require the entire length of the ring. The drawback of this principle is that significant propagation time variations can occur in both transmission directions.

Bidirectional rings: The connections between the individual network elements in this structure are bidirectional. The shorter of the two connections is used as the working line and the longer one as the protection line. If a fault occurs between two network elements A and B, element B initiates a switch-over and controls element A by means of the K1 and K2 bytes of the SOH.

Protection architectures
There are two fundamentally different protection architectures for APS,
- Linear protection --- linear multiplex section protection (linear MSP) point-to-point links.
-Ring protection -- multiplex section shared protection ring (MSSP ring) according to ITU-TG.841 and ANSI T1.105.1 for ring structures.
Both these protection mechanisms make use of alternate circuits or components. The signaling procedures required for the switch-over are transferred in overhead bytes K1 and K2 of the SOH (SDH) or the TOH (SONET).
The three different protection mechanisms
1+1: - Traffic is transmitted simultaneously on the working line and the protection line.
- Both lines transport 100%traffic.
- In the event of a fault, the receiver is switched over to the protection line.
1 : 1: - Traffic is transmitted on one channel only.
- No traffic, or only low-priority traffic, is transmitted on the protection line, 100% protection.
1 : N: - Traffic is transmitted on the working line. No traffic, or only low-priority traffic, is transmitted on the protection line.
- N lines share one protection line.
- In the event of a fault, the protection line takes care of the traffic on the defective channel.
- Common, economical protection method.
Automatic protection switching (APS) is a fault-tolerant topology that is used for providing backup to telecom networks. For network survivability, in the event of failure in a network element or link, APS involves reserving a protection channel with the same capacity as the channel or facility to be protected. In the event of signal-fail (SF) or signal-degrade (SD) condition, the working line switches automatically to the protection line within a few milliseconds.
Network failures, whether due to human error or faulty technology, can be very expensive for users and telecom service providers alike. As a result, the subject of so-called fall-back mechanism is currently one of the most talked about in the telecom world. A wide range of standardised mechanisms is incorporated into synchronous networks in order to compensate for failures in network path/elements and to provide highly-available telecom networks.
The simplest form of protection switching is referred to as 1+1 APS. Each working line is protected by one protection line. If an alarm occurs, a switch-over is initiated at both ends of the connection by the protection agent integrated in the network element. The switch-over is triggered by a defect (e.g. LOS). The switch-over at the opposite end is tripped by a feedback signal in the reverse direction.The 1+1 architecture is 100% redundant. There is one protection line for each working line. The 1:N
architecture is preferred for long-range networks for reasons relating to cost. Here, several working lines share the same protection line.
The 1+1 and 1:N protection mechanisms are standardized in the ITU-T Recommendations. Protection lines can be used for low-priority traffic, which is however interrupted in the event of a switch-over.
Ring protection
- Unidirectional and
- Bidirectional ring structures
Unidirectional rings: The information is only transmitted in one direction. A connection to a
neighboring network element may consequently require the entire length of the ring. The drawback of this principle is that significant propagation time variations can occur in both transmission directions.
Bidirectional rings: The connections between the individual network elements in this structure are bidirectional. The shorter of the two connections is used as the working line and the longer one as the protection line. If a fault occurs between two network elements A and B, element B initiates a switch-over and controls element A by means of the K1 and K2 bytes of the SOH.




1 Comments
6D62F8973E
ReplyDeleteWhatsapp Görüntülü Show
Görüntülü Show
Whatsapp Görüntülü Show Güvenilir